In the evolving landscape of cybersecurity, understanding and mitigating potential threats is paramount. One of the most effective strategies to achieve this is through Threat Modeling, which provides security professionals with a systematic way to identify, analyze, and respond to potential threats.
In this article, I’ll walk you through the fundamental concepts of threat modeling, its necessity in today’s technological world, and how methodologies like STRIDE, PASTA, DREAD, Attack Trees, and VAST play critical roles. By grasping these concepts, you will gain insights into not only safeguarding systems but also understanding the mind of an attacker. Threat modeling is not just a technical exercise; it’s about understanding the context of threats, recognizing vulnerabilities, the probability of occurence, the priority of concern, and prioritizing defenses in line with the objectives of potential adversaries. Ultimately, the objective is to diminish or eradicate the threat.
Over the years, I have seen how a well-executed threat model can make all the difference in preemptively addressing security issues and reducing the attack surface. Throughout this article, we will explore key methodologies utilized in threat modeling, each with its inherent logic and application scenarios. Together, we will demystify the process of threat modeling, demonstrating how it contributes to building secure systems. Whether you are a cybersecurity novice looking to lay a solid foundation or an experienced professional seeking to refine your techniques, this guide aims to equip you with the knowledge you need.
1. Understanding Threat Modeling
There are almost endless possible threats, which is why it’s crucial to use a structured approach to identify the ones that truly matter. Threat modeling is a critical process in cybersecurity that revolves around identifying, enumerating, and prioritizing potential threats to a system. The core purpose of threat modeling lies in providing defenders with a systematic approach to assess the necessary controls or defenses based on the unique nature of their systems. By understanding the probable profile of attackers, the most likely attack vectors, and the assets that hold value to adversaries, organizations can effectively answer vital questions such as, “Where am I most vulnerable?” and “What do I need to safeguard against these threats?”.
Historically, the evolution of threat modeling can be traced back to early military strategies, where the need to anticipate adversary moves prompted systematic assessments of defensive preparations. However, its transition into the realm of information technology began in the 1960s, coinciding with the advent of shared computing. As computer systems became more sophisticated, individuals and organizations recognized the necessity for methodologies that would help identify vulnerabilities and potential exploits. The introduction of concepts like threat trees and attack trees further advanced the field. For instance, Bruce Schneier’s analysis in 1998 illustrated the use of attack trees, creating a visual representation of how an adversary could exploit vulnerabilities to achieve their objectives.
This framework provided a structured way to think through various attack vectors targeting specific systems.
Threat modeling are generally applied in two ways: as a proactive approach during the design phases of the Software Development Lifecycle, or as a reactive approach after the product has already been deployed. Both approaches are valuable, especially since not every threat can be anticipated during the design phase. Moreover, effective threat modeling extends beyond simply recognizing threats. It necessitates a thoughtful approach to risk management, which involves the identification, evaluation, and prioritization of risks complemented by the strategic application of countermeasures.
This is a vital aspect of organizational resilience in the digital age, as the complexity and interdependence of systems increase vulnerabilities. Indeed, organizations must consider not only the direct threats they face but also the indirect ripples resulting from their activities and dependencies on third-party vendors or technologies.
Threat identification can be approached from different angles. One way is to focus on assets, analyzing what harm could be done if they were compromised. Another common approach is to focus on attackers. Understanding who the potential attackers are, how they operate, their objectives, and their Tactics, Techniques, and Procedures (see the MITRE ATT&CK framework) helps in building effective defenses. For instance, if your industry is being actively targeted by a known hacker group, it makes sense to prioritize protections against their methods.”
2. Attack Trees – Visualizing Potential Threats
Like I said, a fundamental tool in the realm of cybersecurity is the concept of attack trees. These are structured, multi-leveled diagrams that visually map out potential attack scenarios on a given asset or target. At the root of the tree lies the ultimate goal of an attacker, while subsequent branches represent all the possible methods by which this goal can be achieved. Each level of the tree breaks down the steps, conditions, and vulnerabilities necessary for successful exploitation. Originating from the works of security experts such as Bruce Schneier and influenced by early work on threat trees, attack trees have become pivotal in both IT security and physical security assessments.
Constructing an attack tree begins with the clear identification of the target or asset under consideration. From here, I suggest you ask, “What does the attacker want to achieve?” This question helps determine the root node. For instance, if the target is a secured computer, the root node might be “Steal Computer.” Then, identify the various methods an attacker could use to achieve this goal. These methods get represented as child nodes. Some common child nodes could include “Pick the Lock,” “Cut the Security Cable,” or “Bribe the Key Holder.” As you delve deeper, you may introduce further sub-tasks or conditions that must be satisfied to fulfill the parent node’s requirements.
Below is an example of an Attack Tree for the StreamFlex VOD Service. The ultimate objective of the attacker is to Steal VODs movies or assets?
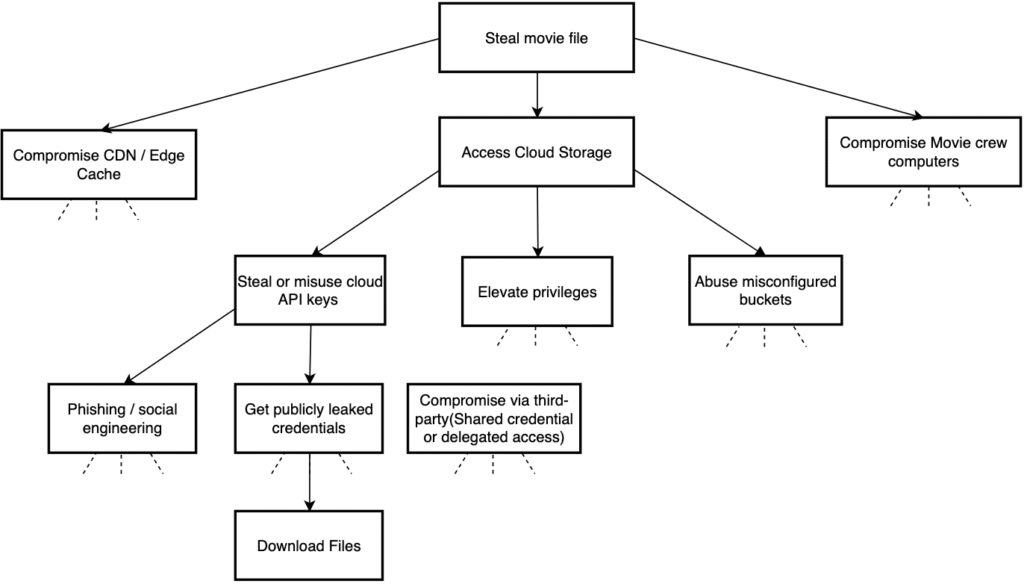
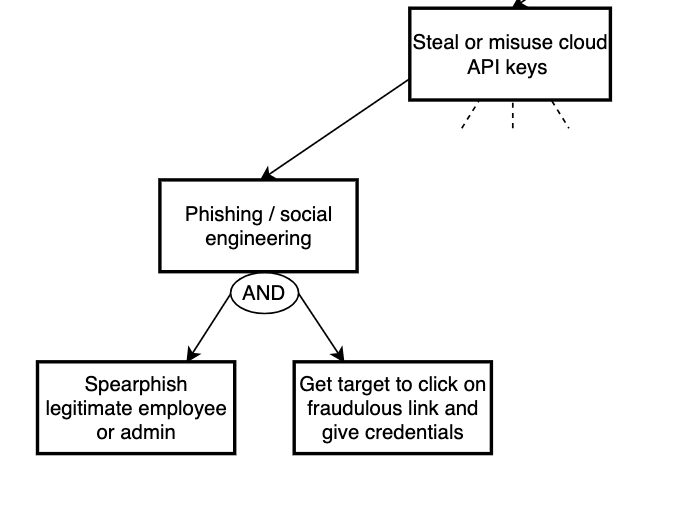
In attack trees we often use simple logic to show how an attacker can reach a goal: some branches require both actions to succeed (an AND condition), while others allow the attacker to take either of several options (an OR condition). For example, one branch might only succeed if an attacker both steals credentials and bypasses network controls those steps form an AND relationship. By contrast, if the attacker can either exploit a vulnerability or trick a user to gain access, those two alternatives form an OR relationship. Explicitly modeling AND/OR relationships makes the attack tree far more precise and lets you analyze which combinations of steps are most likely, most difficult, or most worth defending against. Let’s add an AND condition on our attack tree:
The advantages of employing attack trees are manifold. Primarily, they provide a coherent visual representation of vulnerabilities, making it easier for teams to understand what threats exist. They prioritize risks based on the likelihood of various attack paths, guiding organizations to focus their defensive strategies on the most pertinent threats. Attack trees have real-world applications that transcend just digital systems. For example, military planners use them to simulate ways an adversary might compromise weapon systems or aircraft, while businesses might utilize them to analyze risks to their critical infrastructure.
Attack trees become far more useful when you stop at “what” and start annotating how likely, how costly, and how hard each path is to execute or detect.
Enriching attack trees : What to add and Why it matters?
Attack trees are more actionable when each node carries context. Below are the typical extra attributes:
- Cost — estimated monetary or resource cost for the attacker (e.g., $ for renting infrastructure, or cost in tooling).
- Time — how long the step takes (minutes / hours / days).
- Skill / Complexity — technical skill level required (low / medium / high) or numeric score (1–10).
- Feasibility / Likelihood — probability the step succeeds (qualitative: unlikely/possible/likely or quantitative 0–1).
- Detectability — chance the action will be detected (low/medium/high).
- Impact / Consequence — damage if the node succeeds (low/med/high or $$ / user records exfiltrated).
- Prerequisites — what must already be true (access, tools, insider help).
- Mitigations / Controls — defensive controls that stop or reduce success (MFA, WAF, DLP).
- Confidence — how certain you are about the estimate (low/med/high), useful for readers and decision-makers.
- CVE / technical reference — links to exploits/CVEs if node relies on a known vulnerability.
- Detection signals / SIEM rules — concrete indicators to alert on for that node.
3. STRIDE – A Threat Modeling Framework
In 1999, Microsoft’s development of the STRIDE framework further refined threat modeling by categorizing threats into specific categories:
| STRIDE Category | Simple Definition | Example with StreamFlex VOD Service |
|---|---|---|
| Spoofing identity | Pretending to be someone else to gain access to a system. | An attacker uses stolen employee credentials to log in to the admin portal. Organizations can implement stronger authentication methods such as multi-factor authentication to mitigate this risk. |
| Tampering with data | Altering data in transit or at rest in an unauthorized way. | A hacker or malicious employee modifies billing records in the payment database. Recognizing this threat emphasizes the need for data integrity measures, such as checksums and encryption, to ensure data remains unaltered. |
| Repudiation of activity | Denying an action or activity that was actually performed. It could lead to action being put on a innocent third party. | A employee downloads a movie, but later claims it never happened. Access control, logging & monitoring in place cannot prove them wrong. Implementing thorough logging and audit trails can help mitigate this risk by providing clear evidence of user actions. |
| Information disclosure | Exposing information to unauthorized parties. | A subscriber personal data is leaked through an unsecured API endpoint. An organization can protect against information disclosure by enforcing strong data encryption, strict access controls and need to know princple. |
| Denial Of Service | Making a system unavailable to authorized users. | Attackers flood, overload or use a flaw on the streaming servers that prevent customers from watching movies. Recognizing this threat underscores the necessity for robust network defenses and redundancy measures to maintain availability. |
| Elevation Of Privilege | Gaining higher access rights than initially allowed/intented. | A normal user account exploits a flaw in the network to gain administrator-level access. Understanding this threat calls for diligent access control measures, including the principle of least privilege, to limit user capabilities based on their required roles or Zero Trust principle. |
This mnemonic serves as a practical tool for security professionals to assess potential threats in a more organized and comprehensive manner. Each of these components highlights a specific area of vulnerability within a system that could be exploited by malicious actors, reinforcing the importance of proactive security measures. Understanding these threats is crucial for effective threat modeling as it allows cybersecurity professionals to systematically analyze and safeguard their systems.
The best advantage STRIDE offers is its ability to systematically categorize potential threats across different security properties. By breaking threats into clear, distinct categories, it helps security teams identify and think through risks methodically, ensuring that both technical and process-related vulnerabilities are considered. It’s particularly strong because it ties threats directly to the security goals they impact, making it easier to prioritize mitigations and design controls that address the specific nature of each threat. STRIDE systematic mapping makes it especially effective for software teams:
- Direct Link to Security Goals — each category in STRIDE corresponds to a key security property. This means when a threat is identified, designers immediately understand what security goal is at risk, which guides both architecture and mitigation decisions.
- Structured Threat Analysis — Instead of trying to brainstorm all possible attacks randomly, STRIDE provides a checklist-like framework. Developers can walk through each category methodically, reducing the chance of overlooking subtle but critical threats.
- Early Integration in Design — Because STRIDE works at a system or component level, it can be applied during the design phase, not just after implementation. This allows security controls to be built in from the start rather than patched later, and be aligne with Security By Design principles such as SD3+C (Secure by Design, Secure by Default, Secure in Deployment and Communication).
- Communication Clarity — STRIDE’s categories give a common language for developers, architects, and security teams to discuss threats. This reduces misunderstandings and ensures everyone is aligned on what the risks are and why they matter.
In short, STRIDE doesn’t just list threats; it maps them to what they threaten, how they might occur, and how to prevent them, which makes it extremely practical for designing secure software.
4. VAST – Scalable Threat Modeling for Agile Development
In cybersecurity, organizations are always looking for better ways to weave security into their software development process. This isn’t optional; it’s essential. If you’re in charge, you’ll know that building security in early is far less costly than fixing issues later. One approach that supports this is VAST (Visual, Agile, and Simple Threat) modeling. Unlike older methods that can feel heavy and slow, VAST is designed to fit smoothly into the agile development cycle, making security a built-in part of design and development rather than an afterthought.
VAST prioritizes scalability, enabling teams to address security concerns dynamically as their projects evolve. The traditional model often struggles with complexity, especially in large organizations with diverse teams and varying levels of security awareness. An integral aspect of VAST is its emphasis on collaboration. Security teams often operate in silos, creating a disconnect between developers and security experts. VAST fosters an environment of shared responsibility, where all team members from developers to product owners engage in the threat modeling process. This collaboration is essential for understanding different perspectives about threats, as each role may bring unique insights into the potential vulnerabilities within the system. For instance, while developers can provide details about implementation, product owners can highlight business contexts that may affect threat priorities. This suits well continuous delivery environments, where code is frequently pushed to production.
Let’s take a look at a VAST lifecycle within StreamFlex.
| Step | Employee Actions | Outcome |
|---|---|---|
| Visual – Map the System | Security analyst draws system diagrams; developers verify components; product manager confirms data flows. | Clear visualization of data movement and sensitive areas. |
| Agile – Integrate in Sprints | During feature sprints, team reviews threats; security engineers suggest mitigations; developers implement solutions. | Security is built in as features are developed. |
| Simple – Identify Key Threats | Security analyst lists top threats; developers and QA validate; team prioritizes mitigations. | Focused attention on high-priority, actionable threats. |
| Continuous Monitoring & Updates | Operations reports new changes; security updates threat model; developers implement fixes. | Threat model stays current as the system evolves. |
| Collaboration Across Teams | Cross-functional review meetings; roles clarify responsibilities; mitigation tasks assigned. | Shared understanding of risks and planned actions across all teams. |
In summary, VAST represents a modernization of threat modeling that aligns with the rapid pace of agile development while demanding active, collaborative input from all team members. Its scalability and visual aids make it practical and accessible, ensuring that security remains at the forefront of the software development lifecycle. By integrating VAST practices, organizations can bolster their security posture, ultimately delivering safer applications to their users and standing resilient against emerging threats.
Take a look at this example of planning on one functionality release, drawn from interviews with a few StreamFlex employees.
| Phase | Days | VAST Action / Collaboration | Key Outcome |
|---|---|---|---|
| Planning & Threat Mapping | Mon (Week 1) | Jean (Senior Engineer), Fibou (Product Owner), Lina (Security Architect) map the feature in VAST: data flow, APIs, user touchpoints. Threats identified and assigned. | Living threat model integrated into sprint backlog. Security guides development from day one. |
| Design & Initial Development | Tue–Wed (Week 1) | Jean codes core engine; Lina embeds security checks into CI/CD; Fibou refines requirements based on VAST insights. | Early risk mitigation; architecture decisions aligned with security requirements. |
| Implementation & Continuous Validation | Thu–Fri (Week 1) | Front-end integration begins; CI/CD pipeline continuously runs VAST-driven security checks. | Real-time feedback on security gaps; collaborative adjustments. Jean makes appropriate modification with Lina advisory. |
| Testing & Launch Preparation | Mon–Tue (Week 2) | End-to-end testing guided by VAST; automated CI/CD checks verify authentication, data handling, and API protections. | All mapped threats addressed; mitigations validated before release. Fibou ensure everything is ok. |
| Launch & Post-Release Review | Wed (Week 2) | Feature goes live; team reviews final threat model and pipeline reports; lessons captured for next sprint. | Smart Recommendations deployed securely; threat modeling becomes part of the feature’s story. |
5. PASTA – The Risk-Centric Approach
The PASTA methodology, which stands for Process for Attack Simulation and Threat Analysis, provides a structured, risk-centric approach to threat modeling in cybersecurity. Unlike traditional methods that may prioritize identifying vulnerabilities, PASTA places emphasis on understanding the risk profile associated with specific threats and how they align with business objectives. The aim is to select countermeasures in relation to the value of the assets to be protected. The methodology consists of seven distinct stages. Let’s have a peak on the stages with the StreamFlex VOD company example.
Stage I: Definition of the Objectives for the Analysis of Risks
This stage is about determining what the organization needs to protect. By identifying business goals, key assets, and their importance, security measures can be aligned with the overall direction of the business. For example, Streamflex must allow users to log in, browse, and stream content safely while safeguarding user accounts, content licenses, and customer trust.
Stage II: Definition of the Technical Scope
Clearly outlining the technical environment is essential. This means identifying the infrastructure, applications, and interfaces involved, as well as their architecture and deployment setup. For Streamflex, the scope includes the web app, mobile app, streaming servers, authentication service, content database, and payment system. Outside the scope are user devices and internet service providers.
Stage III: Application Decomposition and Analysis
At this stage, the system is broken down into its individual components. This helps reveal how different parts interact and depend on one another, making it easier to identify areas where threats could affect security or performance. For Streamflex, the key components are login and profiles, content search, streaming servers/CDN, subscription and billing, and DRM/licensing. Data flows between these components should also be mapped.
Stage IV: Threat Analysis
This stage focuses on identifying threats and weaknesses that could impact the system. Rather than just listing risks, PASTA emphasizes simulating how real-world attacks might unfold to understand their impact. For Streamflex, examples include brute force login attempts, DRM bypass for piracy, large-scale API scraping of the catalog, and payment fraud.
Stage V: Weakness & Vulnerability Analysis
After potential threats are identified, the next step is to examine the system’s architecture for weaknesses. This analysis shows which threats are most likely to exploit existing flaws. For Streamflex, findings include the absence of CAPTCHA or rate limiting on login, outdated DRM, lack of API throttling, and weak fraud detection in the billing process.
Stage VI: Attack Modeling & Simulation
Finally, real-world attack scenarios are simulated to test how the system would respond. These exercises turn theoretical threats into practical examples, giving the organization insight into its security posture and the strength of its defenses. For Streamflex, simulations include brute-force account takeovers, exploiting DRM to re-stream movies, bot-driven catalog scraping, and using stolen cards to create fake accounts.
Stage VII: Risk Analysis & Management
Here, the risks created by the identified threats and vulnerabilities are evaluated. The goal is to prioritize which issues to address first by considering both the potential impact and the likelihood of exploitation. For Streamflex, the priorities include adding MFA and rate limits for logins, patching the DRM system, enforcing API keys with throttling, and strengthening fraud detection in billing.
PASTA’s focus on risk assessment means that it not only considers the probability of an attack but also incorporates the motivations and tactics of attackers. Understanding why an attacker might wish to exploit a particular vulnerability provides context to the threat model. By considering the motivations (financial, political, or otherwise), PASTA equips organizations with knowledge of potential attacker behavior, facilitating more informed decision-making about security defenses. It takes a comprehensive view of the system, analyzing architecture, components, applications, and external interfaces to identify where attacks could occur. In addition, its clear, step-by-step framework facilitates communication between technical teams and business stakeholders, ensuring that security considerations are integrated early in the development process rather than added as an afterthought. This combination of depth, practicality, and business alignment makes PASTA a powerful tool for building secure systems from the ground up.
6. DREAD – A Risk Assessment Model
All this threat modeling work leads to the identification of risks. The next important step is to assess those risks in a way that makes sense and supports prioritization. If you’ve read this article I wrote about risk management, you may recall the basic risk matrix that is commonly used everywhere.
But how do you actually determine the impact or likelihood of a threat on your systems?
Among several methodologies, the DREAD framework, standing for Damage, Reproducibility, Exploitability, Affected Users, and Discoverability, has gained popularity for its structured approach to evaluating potential threats. Developed to help teams prioritize risks systematically, DREAD provides a mnemonic to address five key components of risk. Each element plays an essential role in assessing both the severity and likelihood of different threats.
I find the strength of DREAD lies in its quantifiable metrics. Each of the five components can for example be rated on a scale from 1 to 10, allowing for a nuanced representation of risks.
- Damage Potential – How severe the consequences of a realized threat could be. It addresses questions such as “What would the impact be on the organization’s operations or reputation?”
- Reproducibility – Examines how easily an attacker can duplicate an exploit. If an attack mechanism is simple and can be replicated with minimal effort, then the threat level increases significantly.
- Exploitability – Assesses the work needed to launch an attack. This aspect considers the required skills, tools, and resources necessary for an attacker to execute an assault on the system.
- Affected users – What percentage of individuals or systems could be harmed if an attack were successfully executed ?
- Discoverability – Evaluates how easily a weakness can be detected or recognized by an attacker.
One key takeaway from using the DREAD model is its ability to prioritize threats effectively. By summing the ratings across the five categories, organizations can quickly assess which vulnerabilities demand immediate attention and resource allocation. This quantification enables security teams to better allocate their limited resources toward addressing the most pressing threats, ultimately aiming for a more secure operational environment.
However, it’s important to note that the DREAD approach is not without its criticisms. Some experts argue that the inclusivity of the discoverability factor may inadvertently support a false sense of security, potentially promoting the practice of security through obscurity. In response, some organizations have chosen to adapt the framework by omitting this factor altogether or by treating it as a constant high score to mitigate the ambiguity associated with subjective assessments.
6. APPLICATION DECOMPOSITION
Application Decomposition is the process of breaking down an application into its functional components, data flows, and interactions to better understand how it works.
This step is critical in threat modeling (per STRIDE, PASTA, NIST, etc.), because you can’t secure what you don’t understand.
Keys concepts of application decomposition process
| Concept | Description | Example |
|---|---|---|
| Trust Boundary | Where the level of trust changes between two components. Crossing a trust boundary means you need additional controls such as: Validation, Authentication, Encryption, or monitoring. | – User browser → Web server (external → internal) – Web server → Database (app trust → data trust) – Internal microservice → 3rd-party API (internal → external) |
| Dataflow Paths | Dataflow shows how data moves through the system: where it originates, how it’s transformed, and where it’s stored. Mapping flows helps identify points of exposure (e.g., sensitive data in transit, weak links) | – User input → Web App → API Gateway → Microservices → Database – Admin dashboard → Management service → Privileged database queries |
| Inputs Points | All the ways external data enters the application, both expected and unexpected. Attackers exploit weak input points (e.g., SQL injection, XSS, file upload abuse). Every entry must be validated and sanitized. | – HTTP request parameters, headers, cookies – File uploads – API endpoints – Message queues – Background jobs or schedulers |
| Privileged Operations | Any activity or actions that need more privileges than those of a normal account, generally with capability to alter security. If compromised, privileged operations can lead to complete system takeover. | – Database admin queries (DDL, backup/restore) – File system access (read/write/delete) – System calls (spawning processes, network changes) – Role-based operations (admin dashboards, key management) |
Security Stance & Approach
I set this last point aside because it’s somewhat different—it deals more with the overall security posture. When performing decomposition, it’s important to define the application’s security stance (its position toward potential threats) as well as the approach (the measures taken to enforce that stance).
- Security stance
- Never trust input across trust boundaries.
- Data is sensitive by default (protect in transit & at rest).
- Implement defense in depth with multiple layers of controls (input validation, WAF, DB encryption, IAM policies)
- Approach
- Identify all components, trust boundaries, and flows.
- Validate entry points with strict input/output checks.
- Enforce least privilege for users, services, and APIs.
- Apply secure defaults (TLS everywhere, strong authentication, logging).
- Monitor privileged operations and anomaly behaviors.
- Test continuously (code scans, pen tests, threat modeling updates).
Example of application decomposition (Coming soon)
By decomposing an application, you can pinpoint where trust boundaries exist, how data flows across the system, which entry points an attacker could exploit, which operations require special privilege, and ultimately what the overall security posture should be.
The takeway is that Application Decomposition is about making the invisible visible. By explicitly mapping trust boundaries, data flows, inputs, and privileged actions, you gain a structured view to apply the right security controls where they matter most.
7. Final Thoughts
In conclusion, threat modeling is an essential practice in cybersecurity that transcends merely identifying potential risks. As we have explored, methodologies such as STRIDE, PASTA, DREAD, Attack Trees, and VAST provide different frameworks to address various aspects of threat identification and mitigation. By employing these methodologies, organizations can create a comprehensive understanding of their security landscape, prioritize vulnerabilities based on their risk level, and implement effective countermeasures accordingly. The world of cybersecurity is undeniably challenging, but the knowledge gained through threat modeling can significantly empower security professionals in their quest to protect valuable assets. As cyber threats continue to evolve, staying informed and regularly updating threat models will be crucial in maintaining robust defenses. I encourage you to practice threat modeling regularly and integrate these methodologies into your organizational security strategy to foster a proactive security posture.
Don’t forget to take in consideration the Supply Chain in the process of determining risks & aplying apropriate counter measures.
What ‘s Next ?
Let me think about that 😉 . You can tell me what you would like to see next.